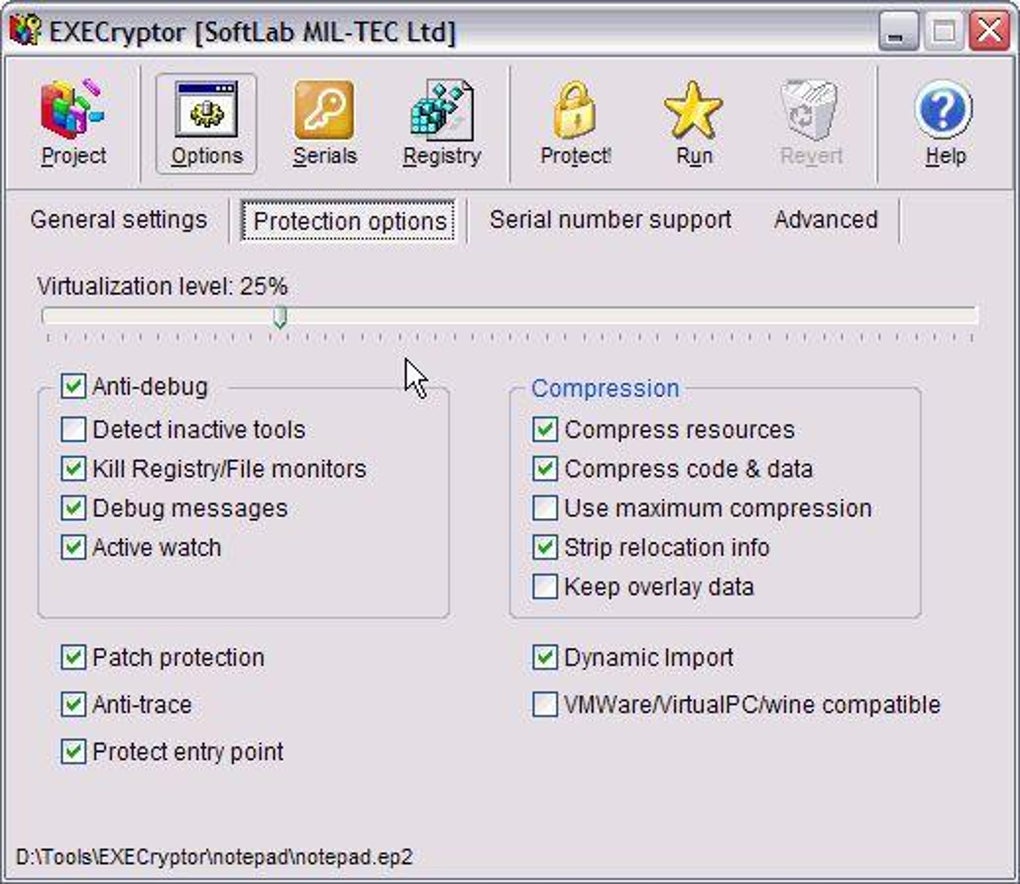
Well, I know that execryptor 2.4.1 is actually quite old. But just click on protect is not enough, this itime i used some sdk, and also put a 5 uses trial, after 5 uses some strings are lost. And also i put some custom things that will make the target more hard. Difficulty: 3/10 Goal: unpack it a.
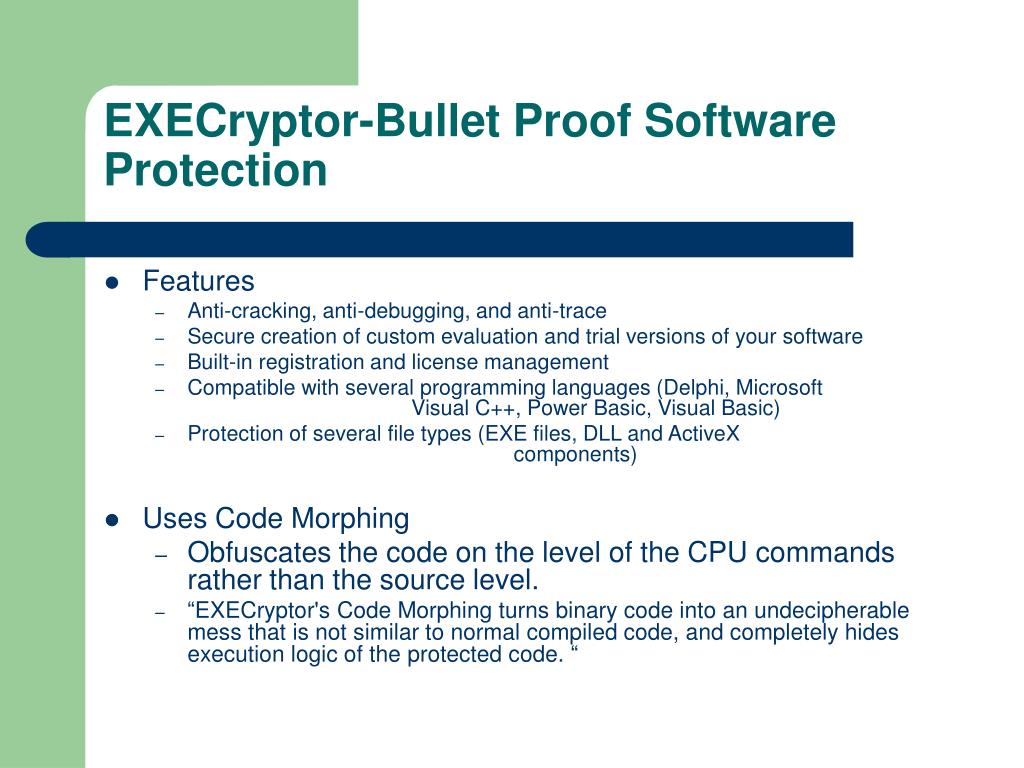
EXECryptor is the strongest and most innovative software security system available. From program protection and cracking avoidance to preventing reverse engineering, analysis, and modifications, EXECryptor has it all. PCK.ExeCryptor will be the cause of complete chaos for anybody who has any encounters with this malicious parasite.PCK.ExeCryptor may also be called any of the following names:PCKExeCryptor,ExeCryptor.PCK,PCK,EXe.Cryptor as well asExeCryptor.No matter what name it goes under the problems are all exactly the same and once your computer has been infected with the malicious PCK.ExeCryptor. EXECryptor allows to work with the short keys of 12/16 characters long and to compress code and ressources of your application. Full Specifications. What's new in version 2.3.9.
Execryptor 2.2.50 | ||
Data | by 'Pnluck', 'Saturn' e 'LittleLuk' | |
11/11/2005 | Published by Quequero | |
Venghino signori, l'é vero, che qui ci sono | Annamo al massimo, annamo a gonfie vele - Pnluck | <<checosa c'è??>> |
.... |
| .... |
Difficoltà | (X)NewBies (X)Intermedio ( )Avanzato ( )Master | |
Introduzione |
Execryptor 2.2.4
- In questo articolo decrivo come fare l'unpacking di execryptor 2.2.50
Visitate il sito di Execryptor per le info su questo packer: http://www.strongbit.com/execryptor.asp

Tools usati |
- Ollydbg, IsDebug&Extra, Olly Invisible, HideDebugger, NtGlobalFlag, OllyDump, AntidetectOllyPatch, RDG
URL o FTP del programma |
- Crackme
Essay |

About EXECryptor
To view somethings about Execryptor visit http://www.strongbit.com/execryptor.asp (most of these techniques are applied through the use of thread)
About Reversing stuff detection
Execryptor uses a lot of tricks to detect ollydbg, and other tools (like softice, filemon, regmon, etc..).This is possible, because Execryptor makes a lot of thread , withus it does a continuous control. For example, isn't possible uses at the same time ollydbg or filemon(not pached) with a software protected by Execryptor.
Those problem is possible resolve with RE-pair 0.6(for regmon, filemon) and AntidetectOllyPatch (for Olly)
About R3 degugger detection
Execryptor uses some trick to verify if he is debugged:
- Control of Beingdebug
- Control of ProcessHeap
- Controll of NtGlobalFlag
- Use of Windows apis
Use CheckRemoteDebuggerPresent and IsDebuggerPresent, look msdn - Use of Seh
With the use of many exception, Execryptor controls if there are Hardware BreakPoints This is the simplest version of seh handler, beacause in other Execryptor controls also the DB register, from 0 to 3 to verify the presence of HD bp and react, therefore use memory bp. - Use of Thread
Execryptor creates a lot of thread to control the presence of Ollydbg, modification of code like bp, etc; to elude these controls in the simpler way, we can do a code injection into CreateThread:
Ollydbg can debug a software protected with Execryptor only with a path and pluings. After the patching and the installation of plugins, we can run a software, here I show how arrive at OEP and how rebuild the iat.
- Prepare Olly to debugging
Patch olly with AntidetectOllyPatch
Open Ollydbg and set these options: Alt+O -> Exceptions ->check: Int3 , SingleStep, Memory access and add Invalid lock sequenze.
Open the option of hide debugger and check IsDebuggerPresent with Unhadled exceptions trick.
Open the option of IsDebug&Extra and check all.
- Find the OEP
Open the menu of NtGlobalFlag and click on 'Set TempBreak on Tls Callback', and 'SET LDR_SHOW_SNAPS'. Now open the software (in this case the crackme) and Olly will break at Tls Callback, and it sets 2 bp, delete them, and set a break-on-access on code section.
Run with alt+f9 the progie and we will break at: Step beyond the jmp, and find a 'cmp ecx,2', because this istruction is the end of decopressing proc: Set a bp on this istruction, push alt+f9 till ecx = 2 and again 3. Now re-set the bp-on-access and remove the bp on 'cmp ecx,2', push alt+f9, if there are exception push always alt+f9, and we'll break at the Oep. Here we can have stolen bytes or not, the difference is visible to eye.With Stolen
There're two method for find stolens:
1) Trace the loader untill the ipotetic oep
2)Use RDG for detect the compiler, analyze the stack and try to do things Dump the progie without rebuild the iat, and analyze this with RDG: is VC5.
Generic opcodes of entrypoint for VC5 is : 'push ebp mov ebp,esp'. So the value of stack addr 12ffc0 is push ebp
Now in the stack there's 0xff = -1(dec) at 12ffbc: 'push -1'. There are also stored two address: 'push 450e60 push 4292c8'. Ok now after the ipotetic OEP there's the installation of a seh handle so: 'push fs:[0]'.
This is the rebuild code(the push eax is overwrite by push fs:[0], but the code is good because eax had the addr of fs:[0]) Now redump with the option of iat rebuild, open the progie with cff or another PE editor, change in Optional Header the base of code to 1000 and delete the Tls directory
Now we have a runnig progie, but the iat isn't all rebuild. To make the dump running also on other PC, you must annul the dword where there's the address of getmodulehandle in loader section in my case 487490. Dump funzionante - Rebuild the IAT
Execryptor uses a new method to call an api, it doesn't use GetProcAddress, but:- Take an hash
- The loader decripts dll's name and it gets the imagebase with GetModuleHandle, it takes the address of export table,after it generates an hash with every api who will be compare with the right_hash, until they will be egual:
- When the loader find the correct hash, it takes the address in memory of api and rewrite the iat_address, push the_return_addr and execute a jmp [iat_addr]
In fact this is a call before the calling: and this is the call after the calling:
- Pnluck, Saturn & LittleLuk
Note finali |
Grazie ai forum Uic e Arteam, Ntoskrnl, Quake2, Quequero, AndreaGeddon il primo ad unpackare execryptor, Shub, Silent, SataNik, LonelyWolf, Zairon, Active85k e tutti i membri di Pmode e Uic
Disclaimer |
Vorrei ricordare che il software va comprato e non rubato, ma cmq potete scaricare na demo di trenta giorni: analizzarla, farle delle modifiche a piacere ed usarla quanto più vi piace ;)